Configuring Accounts and Access
Your configuration determines
whether users can log in with an email address or with a username (with
either method, the user also needs to enter a password). Having users
log in with an email address is recommended, since users can generally
recall their email address more easily than an administrator-assigned
username.
If your previous configuration
required users to log in with a username, you can switch to using an email
address by choosing the email address option. You are prompted to confirm
this change when you save the configuration. You are also notified if
any user accounts do not have email addresses, or if more than one account
has the same email address, and are given the option to download a list
of these users for manual correction. Once you have resolved these issues,
you can choose the email address option again and save the configuration
change.
Important: Choosing the email address option will over-write
any existing usernames. If you want to save the usernames previously assigned
to users, run the Users List report
and export it to CSV. If at some point you choose to switch back to using
usernames, you can import this CSV to restore the usernames.
Choose
the appropriate client or your own organization.
In the Settings screen, from the Edit
menu choose Accounts and Access.
You see a
new set of fields.
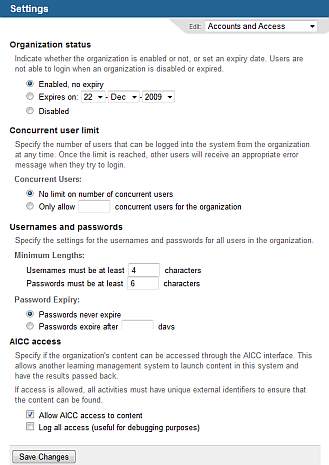
Choose
whether this client is Enabled
(users cannot login to a disabled client).
Optionally,
specify the date on which the client access expires. Once the expiry
date is reached, an organization's users are no longer able to login.
Choose
whether users identify themselves at login by entering an email address
(recommended) or a username and, if a username, specify its minimum
length.
Specify the Minimum
Length for passwords. These limits will be applied when the
user account is created
or a password is
changed. Generally, the longer the password length,
the more secure the user passwords will be.
Note:
A minimum length of eight characters is recommended. Advise users
to use a combination of letters, digits, and symbols in their passwords.
Optionally,
choose the appropriate Password Complexity
(choices configurable by your ).
Optionally,
choose a Password Expiry time
period. When a password expires, at next login the user is prompted
to create a new one.
Optionally,
set a limit on the number of Concurrent
Users this client can have. Once the limit is reached, no additional
users will be able to login. Note that this number refers to distinct
users: if the same user logs in using more than one session, that
will be counted as only a single user.
If appropriate, check Allow
AICC access to content and, for debugging purposes, check Log all access.
Note: Be
sure you have reviewed and understand the requirements
of AICC access section before enabling it. Only turn on AICC logging
when necessary for debugging AICC issues. Leaving logging on when
many users are accessing the external system can slow down AICC access.
Note: Values apply
only to usernames and passwords created
or changed from this point on.